The three zero-day flaws addressed by Apple on September 21, 2023, were leveraged as part of an iPhone exploit chain in an attempt to deliver a spyware strain called Predator targeting former Egyptian member of parliament Ahmed Eltantawy between May and September 2023.
Apple 在 2023 年 9 月 21 日解决的三个零日漏洞被用作 iPhone 漏洞利用链的一部分,试图在 2023 年 5 月至 9 月期间针对前埃及国会议员艾哈迈德·埃尔坦塔维提供一种名为 Predator 的间谍软件。
“The targeting took place after Eltantawy publicly stated his plans to run for President in the 2024 Egyptian elections,” the Citizen Lab said, attributing the attack with high confidence to the Egyptian government owing to it being a known customer of the commercial spying tool.
“目标是在Eltantawy公开表示他计划在2024年埃及选举中竞选总统之后发生的,”公民实验室说,由于埃及政府是商业间谍工具的已知客户,因此高度自信地将这次袭击归因于埃及政府。
According to a joint investigation conducted by the Canadian interdisciplinary laboratory and Google’s Threat Analysis Group (TAG), the mercenary surveillance tool is said to have been delivered via links sent on SMS and WhatsApp.
根据加拿大跨学科实验室和谷歌威胁分析小组(TAG)进行的联合调查,据说雇佣军监视工具是通过短信和WhatsApp上发送的链接提供的。
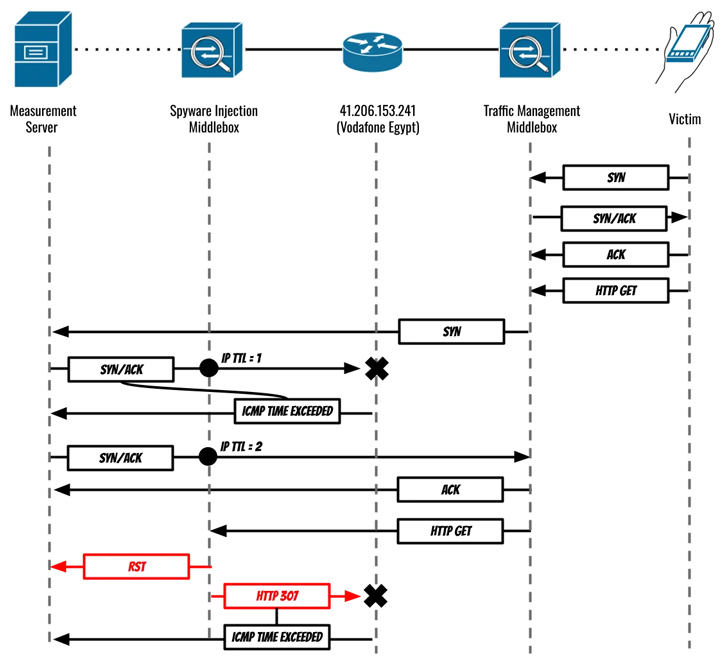
“In August and September 2023, Eltantawy’s Vodafone Egypt mobile connection was persistently selected for targeting via network injection; when Eltantawy visited certain websites not using HTTPS, a device installed at the border of Vodafone Egypt’s network automatically redirected him to a malicious website to infect his phone with Cytrox’s Predator spyware,” the Citizen Lab researchers said.
“在 2023 年 8 月和 9 月,Eltantawy 的沃达丰埃及移动连接被持续选择通过网络注入进行定位;当Eltantawy访问某些不使用HTTPS的网站时,安装在沃达丰埃及网络边界的设备会自动将他重定向到恶意网站,用Cytrox的Predator间谍软件感染他的手机,“公民实验室的研究人员说。
The exploit chain leveraged a set of three vulnerabilities – CVE-2023-41991, CVE-2023-41992, and CVE-2023-41993 – which could allow a malicious actor to bypass certificate validation, elevate privileges, and achieve remote code execution on targeted devices upon processing a specially crafted web content.
漏洞利用链利用了一组三个漏洞(CVE-2023-41991、CVE-2023-41992 和 CVE-2023-41993),这可能允许恶意行为者在处理特制 Web 内容时绕过证书验证、提升权限并在目标设备上实现远程代码执行。
Predator, made by a company called Cytrox, is analogous to NSO Group’s Pegasus, enabling its customers to surveil targets of interest and harvest sensitive data from compromised devices. Part of a consortium of spyware vendors called the Intellexa Alliance, it was blocklisted by the U.S. government in July 2023 for “enabling campaigns of repression and other human rights abuses.”
由一家名为Cytrox的公司制造的Predator类似于NSO集团的Pegasus,使其客户能够监视感兴趣的目标并从受感染的设备中收集敏感数据。作为间谍软件供应商联盟的一部分,它于 2023 年 7 月被美国政府封锁,罪名是“促成镇压和其他侵犯人权运动”。
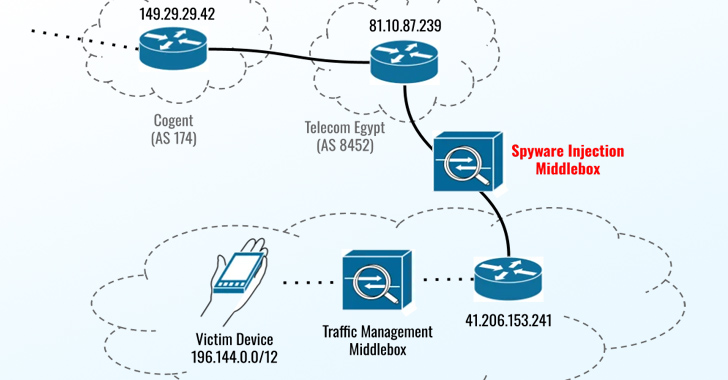
The exploit, hosted on a domain named sec-flare[.]com, is said to have been delivered after Eltantawy was redirected to a website named c.betly[.]me by means of a sophisticated network injection attack using Sandvine’s PacketLogic middlebox situated on a link between Telecom Egypt and Vodafone Egypt.
该漏洞托管在名为sec-flare的域上。com,据说是在Eltantawy被重定向到一个名为c.betly的网站后交付的。我通过使用位于埃及电信和沃达丰埃及之间链路上的Sandvine的PacketLogic中间盒进行复杂的网络注入攻击。
“The body of the destination website included two iframes, ID ‘if1’ which contained apparently benign bait content (in this case a link to an APK file not containing spyware) and ID ‘if2’ which was an invisible iframe containing a Predator infection link hosted on sec-flare[.]com,” the Citizen Lab said.
“目标网站的正文包括两个iframe,ID ‘if1’,其中包含明显良性的诱饵内容(在本例中是指向不包含间谍软件的APK文件的链接)和ID ‘if2’,这是一个不可见的iframe,其中包含托管在sec-flare上的Predator感染链接。com,“公民实验室说。
Google TAG researcher Maddie Stone characterized it as a case of an adversary-in-the-middle (AitM) attack that takes advantage of a visit to a website using HTTP (as opposed to HTTPS) to intercept and force the victim to visit a different site operated by the threat actor.
Google TAG研究员Maddie Stone将其描述为中间对手(AitM)攻击的案例,该攻击利用使用HTTP(而不是HTTPS)访问网站来拦截并迫使受害者访问由威胁行为者运营的其他站点。
“In the case of this campaign, if the target went to any ‘http’ site, the attackers injected traffic to silently redirect them to an Intellexa site, c.betly[.]me,” Stone explained. “If the user was the expected targeted user, the site would then redirect the target to the exploit server, sec-flare[.]com.”
“在这次活动中,如果目标转到任何’http’站点,攻击者会注入流量以静默地将他们重定向到Intellexa站点,c.betly[。我,“斯通解释道。“如果用户是预期的目标用户,那么该站点会将目标重定向到漏洞利用服务器sec-flare[。“唰唰�
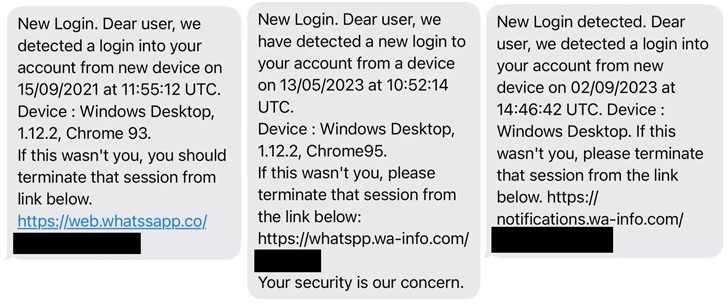
Eltantawy received three SMS messages in September 2021, May 2023, and September 2023 that masqueraded as security alerts from WhatsApp urging Eltantawy to click on a link to terminate a suspicious login session originating from a purported Windows device.
Eltantawy 分别于 2021 年 9 月、2023 年 5 月和 2023 年 9 月收到三条短信,伪装成来自 WhatsApp 的安全警报,敦促 Eltantawy 单击链接以终止源自据称 Windows 设备的可疑登录会话。
While these links don’t match the fingerprint of the aforementioned domain, the investigation revealed that the Predator spyware was installed on the device approximately 2 minutes and 30 seconds after Eltantawy read the message sent in September 2021.
虽然这些链接与上述域的指纹不匹配,但调查显示,在 Eltantawy 阅读 2021 年 9 月发送的消息后大约 2 分 30 秒,设备上安装了 Predator 间谍软件。
He also received two WhatsApp messages on June 24, 2023, and July 12, 2023, in which an individual claiming to be working for the International Federation for Human Rights (FIDH) solicited his opinion on an article that pointed to the website sec-flare[.]com. The messages were left unread.
他还在 2023 年 6 月 24 日和 2023 年 7 月 12 日收到了两条 WhatsApp 消息,其中一名自称为国际人权联合会 (FIDH) 工作的个人就一篇指向网站 sec-flare[..com。这些消息未被阅读。
Google TAG said it also detected an exploit chain that weaponized a remote code execution flaw in the Chrome web browser (CVE-2023-4762) to deliver Predator on Android devices using two methods: the AitM injection and via one-time links sent directly to the target.
Google TAG表示,它还检测到一个漏洞利用链,该漏洞利用Chrome网络浏览器中的远程代码执行缺陷(CVE-2023-4762)武器化,使用两种方法在Android设备上交付Predator:AitM注入和通过直接发送到目标的一次性链接。
CVE-2023-4762, a type confusion vulnerability in the V8 engine, was anonymously reported on August 16, 2023, and patched by Google on September 5, 2023, although the internet giant assesses that Cytrox/Intellexa may have used this vulnerability as a zero-day.
CVE-2023-4762 是 V8 引擎中的一个类型混淆漏洞,于 2023 年 8 月 16 日匿名报告,并于 2023 年 9 月 5 日由 Google 修补,尽管这家互联网巨头评估 Cytrox/Intellexa 可能已将此漏洞用作零日漏洞。
According to a brief description on the National Vulnerability Database (NVD), CVE-2023-4762 concerns a “type confusion in V8 in Google Chrome prior to 116.0.5845.179 [that] allowed a remote attacker to execute arbitrary code via a crafted HTML page.”
根据国家漏洞数据库 (NVD) 的简要描述,CVE-2023-4762 涉及“116.0.5845.179 之前的 Google Chrome V8 中的类型混淆,允许远程攻击者通过构建的 HTML 页面执行任意代码。
The latest findings, besides highlighting the abuse of surveillance tools to target the civil society, underscores the blindspots in the telecom ecosystem that could be exploited to intercept network traffic and inject malware into targets’ devices.
最新调查结果除了强调滥用监控工具针对民间社会外,还强调了电信生态系统中的盲点,这些盲点可能被用来拦截网络流量并将恶意软件注入目标的设备。
“Although great strides have been made in recent years to ‘encrypt the web,’ users still occasionally visit websites without HTTPS, and a single non-HTTPS website visit can result in spyware infection,” the Citizen Lab said.
“尽管近年来在’加密网络’方面取得了长足的进步,但用户仍然偶尔访问没有HTTPS的网站,一次非HTTPS网站访问都可能导致间谍软件感染,”公民实验室说。
Users who are at risk of spyware threats because of “who they are or what they do” are recommended to keep their devices up-to-date and enable Lockdown Mode on iPhones, iPads, and Macs to stave off such risks.
建议因“他们是谁或他们做什么”而面临间谍软件威胁风险的用户使其设备保持最新状态,并在 iPhone、iPad 和 Mac 上启用锁定模式以避免此类风险。